MISP 2.4.110 released (aka local-tags and new MISP modules supporting MISP standard format)
MISP 2.4.110 released
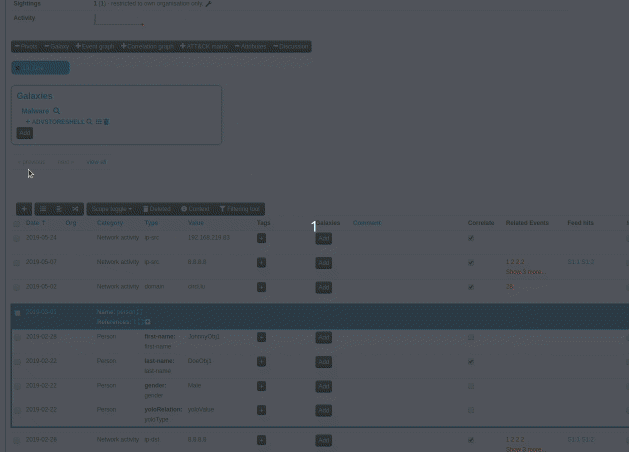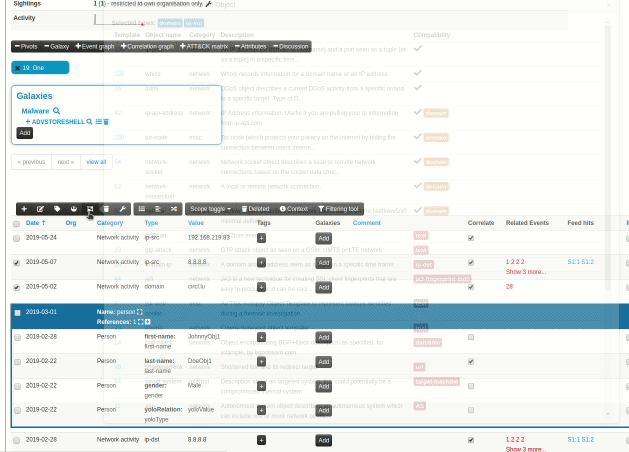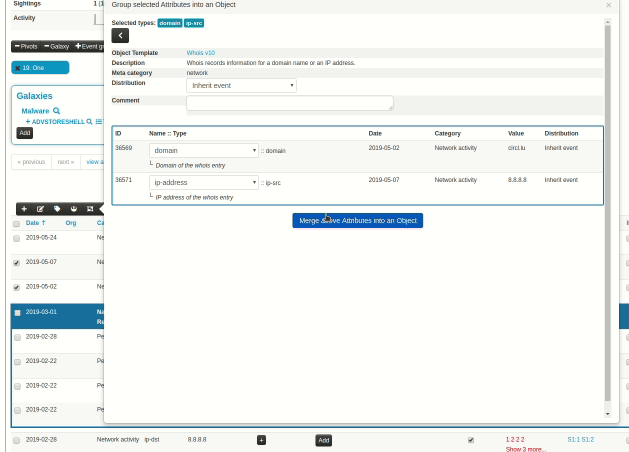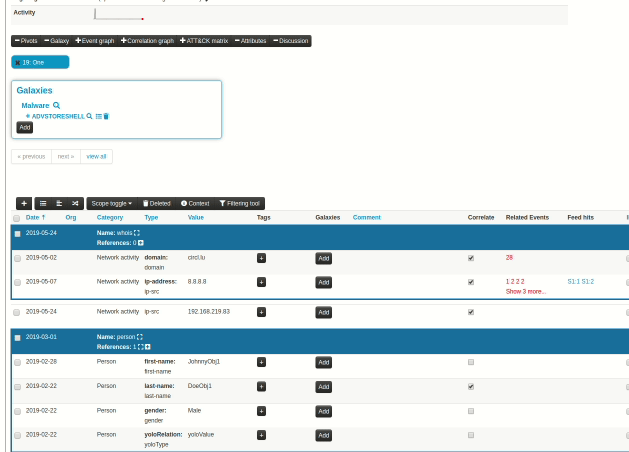
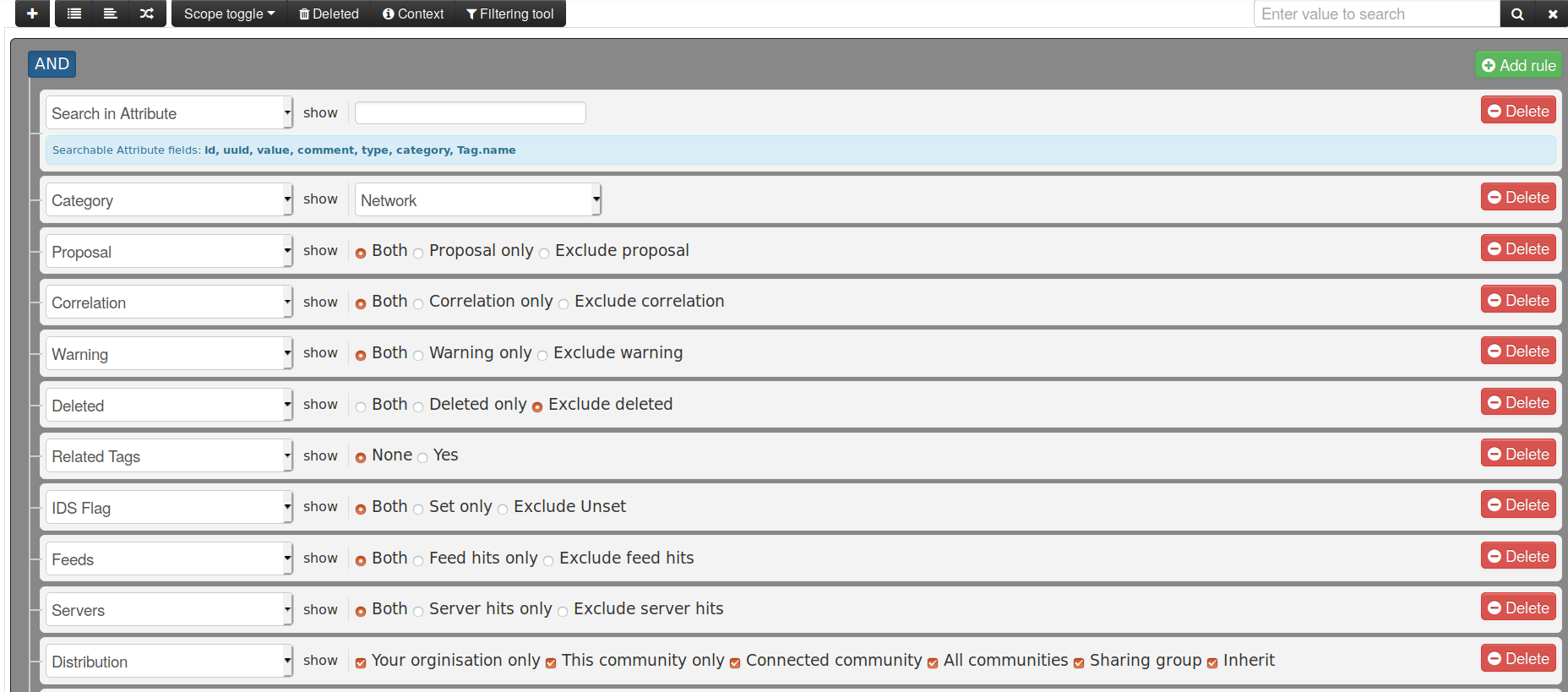
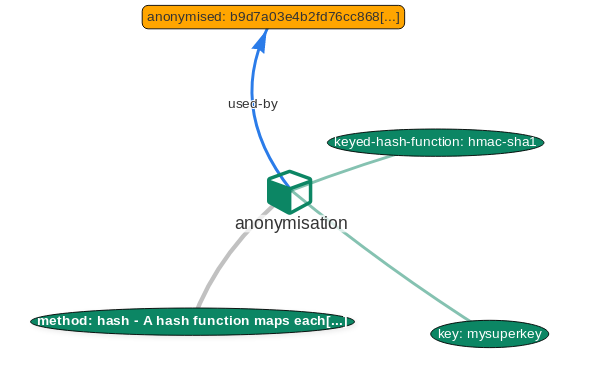
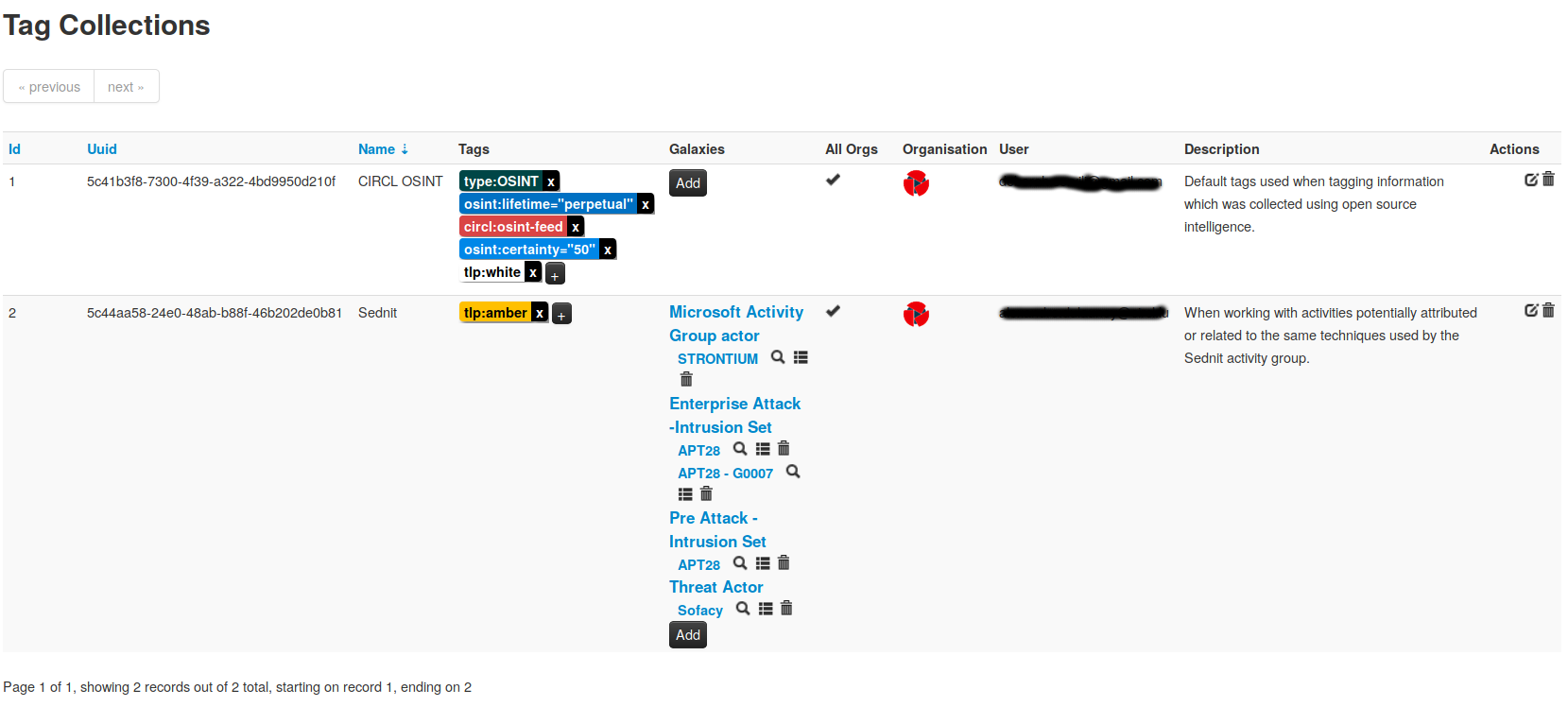
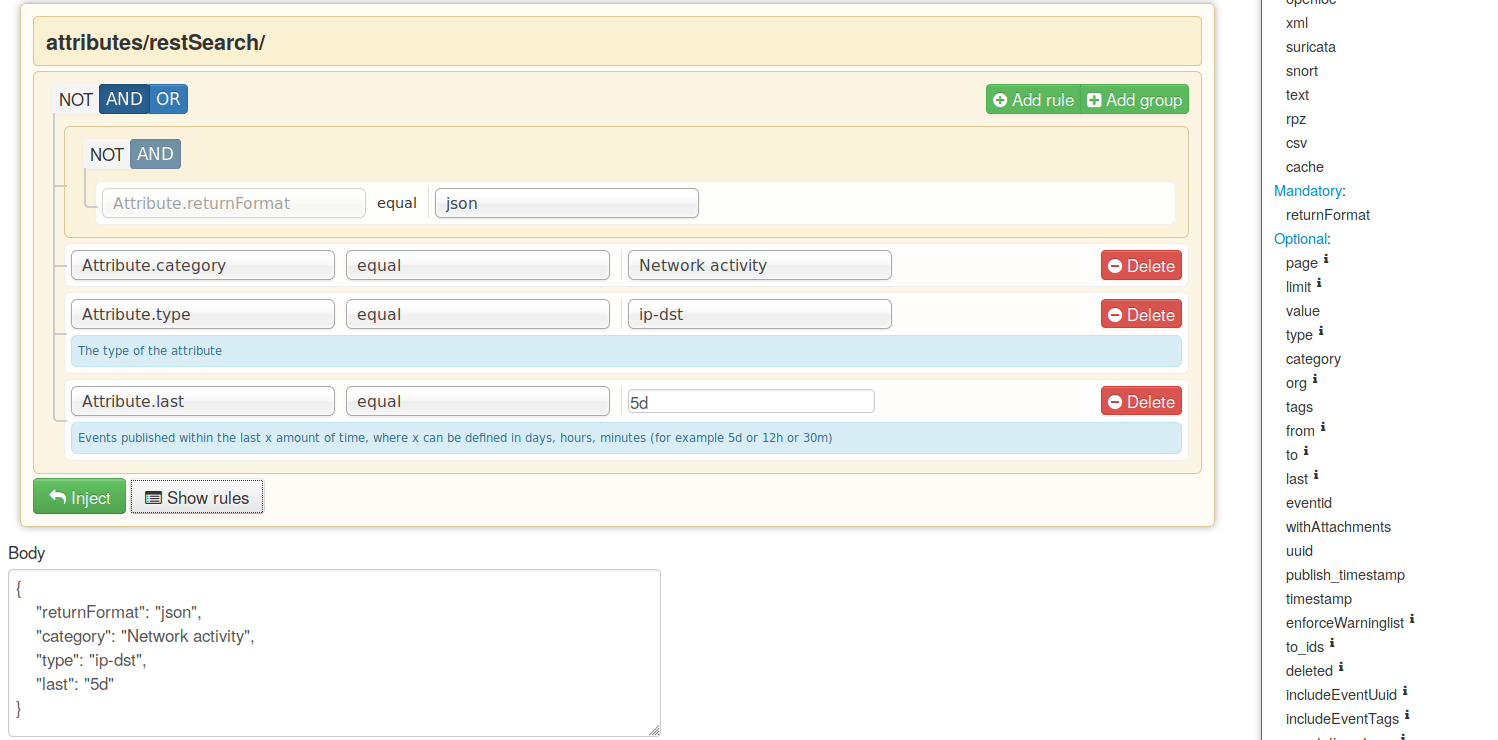
A new version of MISP (2.4.110) has been released with a host of new features, improvements, many bugs fixed and one security fix. Even under the searing summer sun, the MISP-project team is hard at work, whilst enjoying some cocktails (with or without booze).